
Cybersecurity
In an ever-increasingly digital world, how do you protect your business? Cyberattacks are silent and unpredictable and can lead to the loss of an organization’s critical information, which may be irrecoverable if not adequately protected. Are you willing to take that risk?
Protect your business from current and future threats and reduce your risk exposure.
For who?
In a more digital world, cyber threats numbers are growing at an alarming rate. For that reason, your business needs to ensure resilience, protection and reliability.
Reinforce resilience
Mitigate the risk of human failure
Protect and strengthen the business reputation
Digital Protection
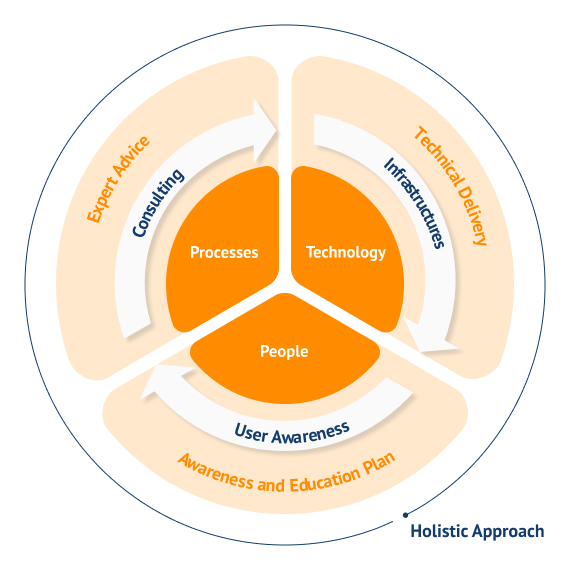
Check and protect your business on three main vectors: processes, technology, and people. We design, implement, and document cyber-resilience projects tailored to your company’s needs allowing to reduce risk exposure.
-
 Specialized cybersecurity advisory
Specialized cybersecurity advisory -
 Designing and implementing continuous improvement processes
Designing and implementing continuous improvement processes -
 Defining security strategies based on application or computer system lifecycle
Defining security strategies based on application or computer system lifecycle
Methodology
Our methodology allows us to support organizations in a transversal mode, focused on people, technology and processes.
Contact us
Protect your company against current and future threats. As cybersecurity experts, we can help you improve your business resilience.
